#
Due to the involvement of sensitive information, please forgive me.
Recently, there was a project where information was collected on a certain target unit, which is a mail system.
Target: XXX.gov.cn a certain government-level target
System: Self-built mail service system
The system has a slider verification, so web brute-forcing the email is not very effective. At the same time, the server does not have a real IP that can be used for protocol brute-forcing.

Then, information was collected on this system, and it was found through Tianyancha that the supplier of the target's assets is XXXX Company. This company has contracted most of the third-party system development for this municipal unit, making it a very valuable supplier. The idea was quickly changed to target the supplier.
0x2 Supplier Information Collection#
XX Technology
Website: testteam.com
Legal representative email: 188888888_@_qq.com
Legal representative phone number: 18888888888
Subsidiary Company
XXX() Technology
Website: 1.testteam.com
Legal representative email: 13333333_@_qq.com
Legal representative phone number: 13333333333
The only information that can be found through public channels is this. After querying the collected information assets, it was found that there was nothing useful, so it was decided to start from the website.
Scanning the domain only yielded one IP, and there were no extra IPs in the historical resolution. A full port scan was conducted on this IP, and the only open ports were 3389 and 443, 80, and it is a cloud server, with no extra assets in the subdomains.

However, it was found that the website directory provided an OA login interface.

Using weak password login attempts, after entering the account, it returned blank, but in fact, it was a successful login.

However, the login process logic might have some issues, requiring manual modification of requests and access paths to reach the backend.

Upon reaching the supplier's backend, no useful information was found, and the assets were scarce, so it was decided to target the employees.
As we all know, GitHub developers often like to upload project materials, including leaked account passwords in some scripts. Therefore, I collected suspected employees of the company on GitHub.

His project repository contains the company's manual, and I also found a bookmark and password in another project, deciding to dig deeper into this employee.
0x3 Employee Information Collection#
From his project code, many are local localhost IPs, but a few bookmark addresses caught my attention, one of which is the Xiaomi official website.
Based on the existing assets, this employee uses three emails, from Sina and QQ. It is easy to guess which email he mainly uses, for example, checking Xiaomi's binding.
Using the password recovery function, I obtained the bound email for Xiaomi, and also acquired the commonly used email of this employee.
Using the previously obtained password, I logged into NetEase Mail Master with the NetEase email, briefly looked at the emails exchanged, and found nothing of great value. To avoid alarming the target, I set up email forwarding for that email.

Then I used that email to log into the Xiaomi account.

From the personal shipping address, I obtained the real name and physical address, confirming that it belongs to the company's physical address. I then used Xiaomi Cloud Services to locate the individual.

Next, I used the address from the email to log into 51job to view the employee's resume.

I also confirmed from the employee's historical information that he was once an employee of the target company.
At the same time, I obtained some platform accounts from the QQ email.

I logged into several platforms from these platforms, but none were related to the target.

At this point, I was already pondering a question: I have gathered so much information, but I still do not know what channels the target company's OA or internal communication uses. I cannot get from individuals to the inside. There must be a communication place internally, but so far, apart from the skill manual I saw at the beginning, I have not seen any information about the company. Simply collecting such information is of no use.
0x4 Collaborative Software Information Collection#
- Tencent Docs
- Kingsoft Office
- DingTalk
- Yuque
- WeChat Work
- Weiyun
- Feishu
The next day, I continued to search for supplier information.
I was thinking, since the official website has no business or OA, what platform do they use for communication?
Here I tried software like Yuque/Feishu/Youdao Cloud Note/DingTalk/Evernote/WPS. After several attempts, I was able to log into most accounts with the obtained password. I could log into DingTalk and WeChat Work, but both required phone number verification, so they might be using one of those two, but I couldn't proceed.

Yuque and Tencent Docs had nothing written, so there was nothing to do.

Weiyun had no company information apart from personal data, which was also useless.
So only WPS was left.
At this point, an interesting situation arose. Kingsoft Docs must have been used to some extent. I could reset his account to his commonly used password because his password patterns were similar. I bet he would not think much if he found the password wrong and tried his common password.
However, the password modification for WPS was never sent to my forwarding email, and then I used the QQ account bound to GitHub + common password to log in.


After logging in, yes! Finally, there was information about the target assets, which was a list of the company's employee directory.
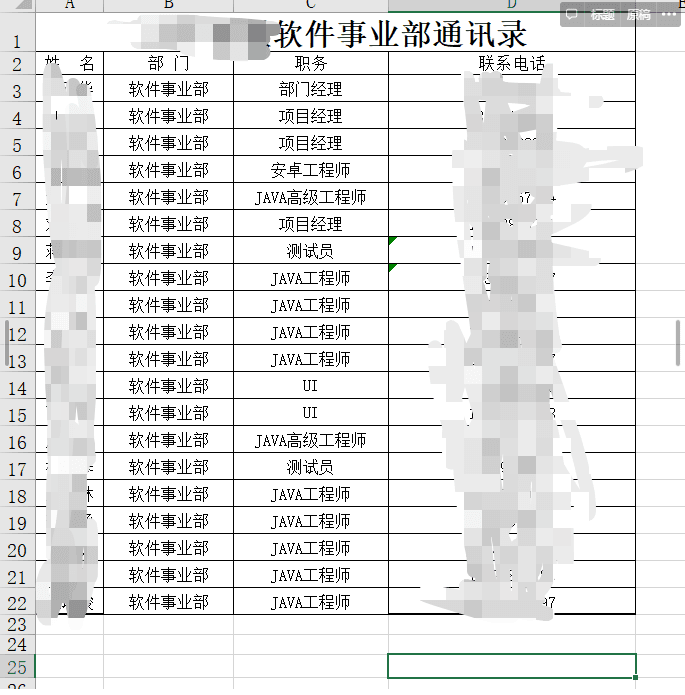
Actually, at this point, I was not prepared to continue because I could not determine the communication platform used by the target, and the target assets were scarce. It would not be good to continue breaking through from the employees, as it is likely to be a waste of time.
Thinking back on the path taken from the employees, I was quite lucky. If any email had set up a two-step login verification or if he had strengthened his password rules a bit, I would not have obtained this directory. This employee had basically obtained all the information, and I felt that DingTalk might be used, but DingTalk requires facial recognition to log in.
0x5 Obtaining the Target#
At this point, I began to reflect that this path seemed to be unable to obtain the target. I had not obtained the source code, nor had I obtained the system password, and there were no significant breakthroughs with the supplier.
Seeing that he used GitHub quite a lot, I decided to change his GitHub password to access the repository code.
Using the Sina email I initially controlled, I changed his password to his commonly used password and successfully logged in.

![]()
While reviewing all his repository codes, I unexpectedly found a password for the target system. The password was a common one, and the account was relatively long, which was extremely lucky.
I successfully logged in with that account, and it even had administrator privileges.

Finally, I obtained backend permissions.
0x6 Summary#
This was not a technical penetration; luck was the primary factor. Everything was interconnected, and just go for it.